High Level Architecture
Our architecture enables secure, private, and scalable financial transactions through a private, permissioned ledger that can be implemented as a sidechain or as a layer 2. At its core is a Zero-Knowledge Composable Smart Contract (zk-CSC) system that supports confidential, atomic operations. Hamsa’s solution extends standard token protocols (e.g., ERC20, ERC1155) with advanced methods — such as privateReserveAmount and privateRollBackAmount — ensuring transaction details remain visible only to the involved parties. ZK-CSC is the first smart contract framework to provide full privacy using zero-knowledge proofs (ZKPs) while maintaining composability. It can process both plaintext logic and encrypted data, guaranteeing atomicity, privacy, and interoperability.
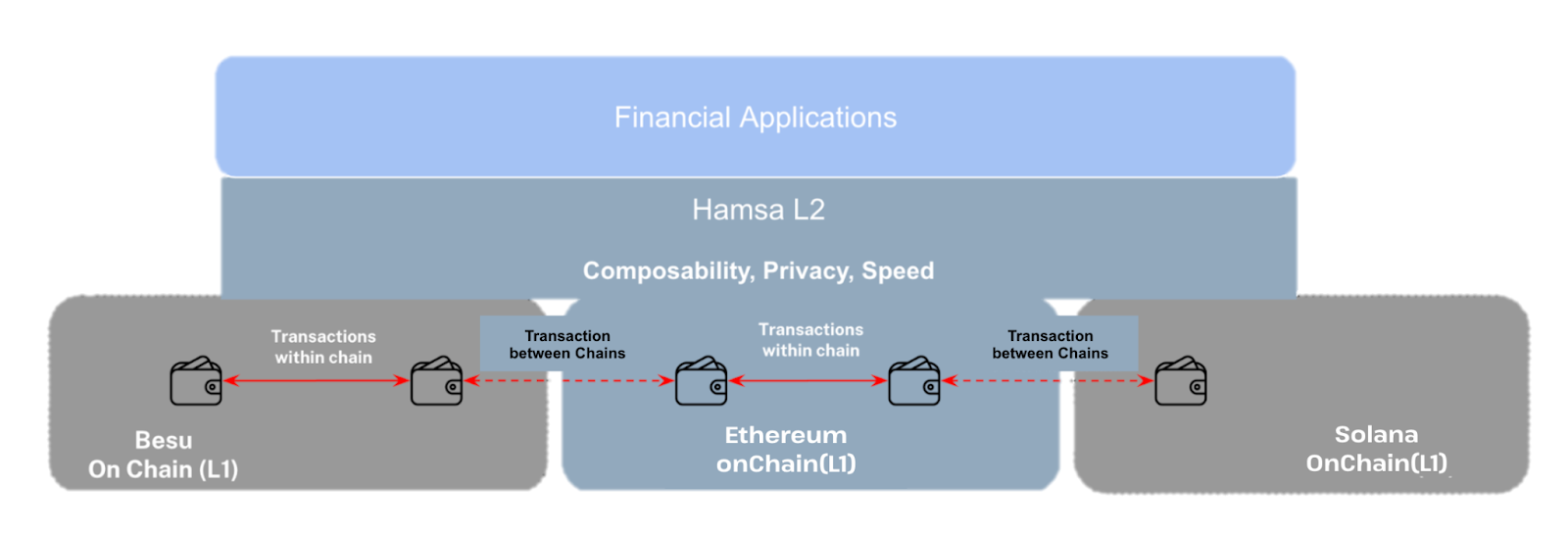
The high-level architecture, depicted in Figure 1, features banking and financial applications interacting with the Hamsa ledger as a Layer 2 blockchain. Hamsa ledger supports both public and private EVM-compatible transactions. When implemented as a sidechain, the ledger optionally commits network state snapshots to a distinct EVM blockchain. This process cryptographically anchors finalized transactions on Hamsa's ledger. As a result, any adversarial attempt by a supermajority to reverse or alter the transaction history of the Hamsa network would be demonstrably inconsistent with the immutable state recorded on the secondary EVM chain.
The Layers
The Layers's main characteristics are described below:
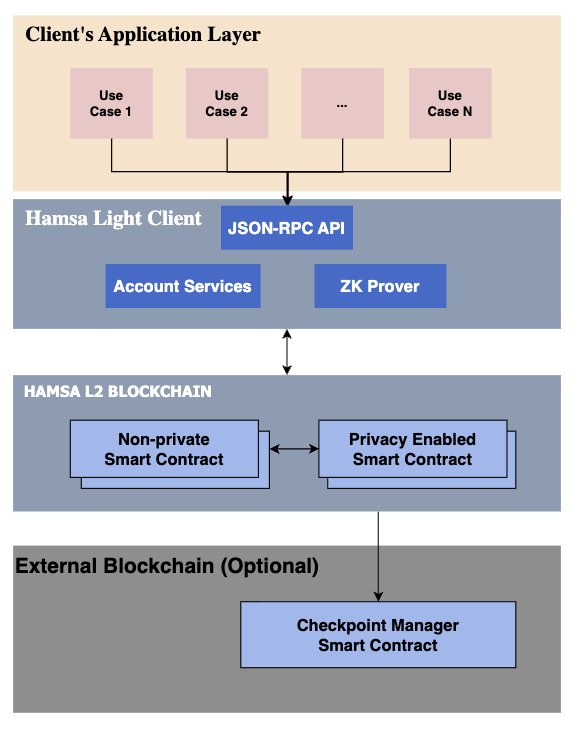
Hamsa Light Client:
- Purpose: Store locally the private information and operate the privacy-enabled smart contracts.
- Services:
- JSON-RPC API: an accessible API following the exact standards of all EVM blockchain nodes, it's a convenient way to send private and non-private transactions to the L2, as well as query its state.
- ZK Prover: a specialized zero knowledge prover software with an embedded enhanced version of the microsoft NOVA ZK-Folding scheme.
- Account Services: the brain of the operation, this module stores the relevant information, interacts with the local L2 node, controls and coordinates every other service within this layer.
- Type: Bundle of microservices (e.g. Helm Chart) installed in each client's infrastructure.
Hamsa Blockchain:
- Purpose: Handles confidential transactions with privacy and scalability.
- Services: All the privacy enabled and non-private smart contracts that compose to provide the services needed by the Client's applications.
- Type: EVM-compatible permissioned zero-gas high-speed blockchain utilizing Microsoft NOVA ZKP Folding scheme and zk-Composable Smart Contracts (zk-CSC).
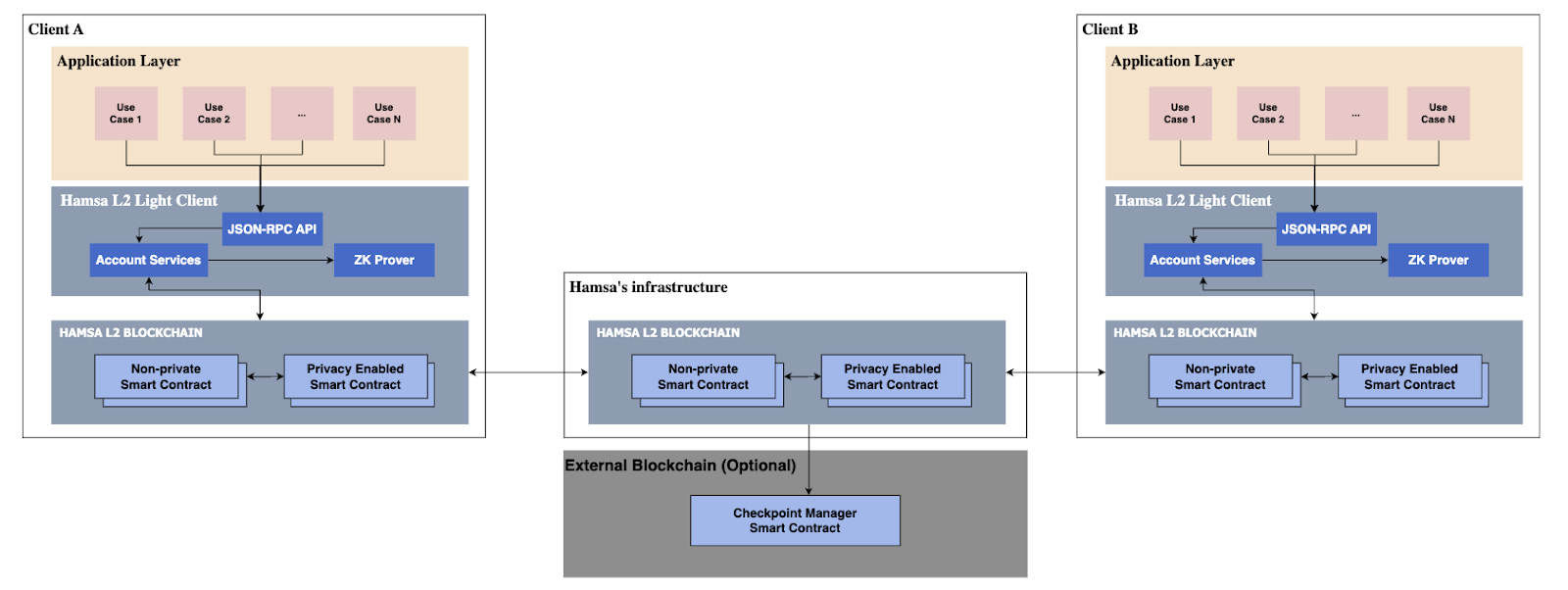
External Blockchain (Optional):
- Purpose: Serves as a trust anchor.
- Services: the checkpoint manager smart contract serves as unbreakable storage for the L2 state checkpoints.
- Type: EVM-compatible blockchain.
Deployment
The deployment architecture showcases two distinct clients, Client A and Client B, each maintaining its own independent stack consisting of an Application Layer, a Hamsa Light Client and their own Hamsa node. These light clients interface with the core Hamsa Blockchain infrastructure. Notably, Hamsa provides an optional service for connecting its blockchain with an external blockchain via a Checkpoint Manager Smart Contract. This optional component allows clients leveraging the Hamsa network to potentially benefit from the security and immutability of a chosen external blockchain.